Hacker attack: understand the risks and how to protect yourself
The term "hacker attack" refers to malicious attempts to compromise digital systems, steal data, disrupt operations, or obtain illicit financial gain. With the increasing digitalization of businesses, these attacks have become more frequent, sophisticated, and devastating.
In recent months, three incidents have brought this issue to the forefront:
- Hacking into C&M Software, a company linked to the PIX system, with the theft of over R$ 500 million;
- Dell's data leak of 1.3 TB compromised customer records and internal documents.
- Exploitation of vulnerabilities in Microsoft SharePoint servers , impacting hundreds of companies.
These cases reinforce a harsh reality: no company is immune, not even tech giants.
Understanding the different types of attacks is the first step to protecting yourself:
1. Phishing
- Scams disguised as legitimate emails, messages, or websites, designed to trick users into giving away passwords and personal data.
- Very common in bank fraud and corporate intrusions.
2. Ransomware
- Criminals seize data and demand ransom in cryptocurrency.
- Recent example: the ThreatSec group claimed responsibility for the leak at Dell, although the exact nature of the leak is still under investigation.
Read also: "Ransomware survival guide: how to act before, during and after an attack?"
3. Social engineering attacks
- They involve the psychological manipulation of people to gain privileged access.
- This was the technique used in the C&M Software case (with the cooperation of an "insider") .
4. Exploitation of vulnerabilities
- Attackers exploit known (or unknown) vulnerabilities in outdated or misconfigured systems and software, as in the case of Microsoft where outdated SharePoint servers were the entry point.
5. Insider attacks
- Current or former employees who sell access credentials or intentionally collaborate with criminals.
Several factors explain the growth of these digital crimes:
| Factor | Description |
| Accelerated digitization | Companies migrated to digital without investing proportionally in security |
| Most valuable data | Personal, corporate, and banking information is highly lucrative |
| Insiders (Internal Threats) | Internal threats have been growing and require special attention |
| Lack of cybersecurity culture | Training and processes are neglected. Human error remains the weakest link |
| Use of AI by criminals | Hackers are now using artificial intelligence to automate attacks |
According to an article by TecMundo , Dell suffered a ransomware attack in June 2025 that resulted in the leakage of 1.3 terabytes of data . Among the exposed files were customer information, internal documents, and purchase records.
The attack was carried out by a hacker group called ThreatSec , which exploited a vulnerability in the company's support server. The incident directly impacted the brand's reputation and highlighted the importance of protecting exposed environments and constantly monitoring digital assets .
According to InfoMoney , around the same time, Microsoft was the target of a hacker attack that exploited vulnerabilities in SharePoint servers , impacting companies that used outdated versions of the platform .
The vulnerability allowed unauthorized access to clients' corporate servers, generating global concern about the lack of updates and monitoring in critical applications . This case reinforces the importance of maintaining secure, up-to-date, and well-configured environments .
In an article by Exame magazine , the hacker attack on C&M Software , a supplier connected to the PIX ecosystem, was described as one of the biggest scams ever recorded in the country. An insider sold credentials and facilitated the theft of approximately R$ 1 billion in reserve accounts from the Central Bank, with roughly half of that amount belonging to a single institution.
The case highlighted serious flaws in authentication, social engineering, and a lack of continuous monitoring. Above all, it showed that it is not enough to protect the company itself; it is also necessary to safeguard the chain of partners and suppliers .
This type of crime, known as a supply-chain , is growing precisely because it exploits third parties as a gateway to critical environments.
Here are five strategic pillars to reduce the risk of intrusions:
1. Implement multi-factor authentication (MFA)
- Even if the password is stolen, access is blocked with this additional layer of protection.
- Skyone offers integration with robust identity systems and centralized access management.
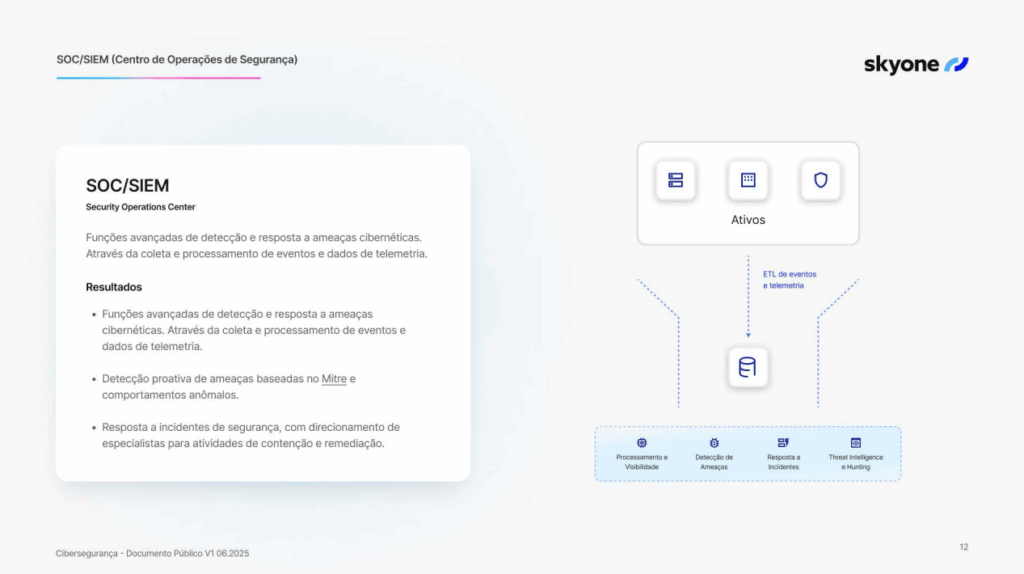
2. Monitor 24/7 with a SOC
- The Security Operations Center (SOC) detects and responds to threats in real time, with proactive analysis and visibility dashboards.
- With Skyone's SOC , companies have access to a team of experts who work continuously to reduce operational risks.
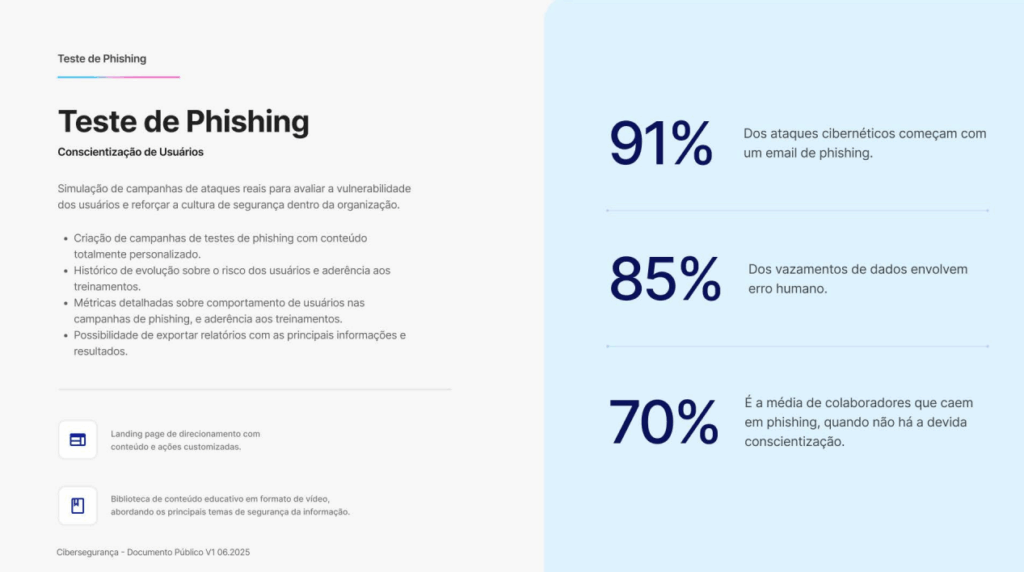
3. Conduct phishing simulations
- Controlled training and testing help to strengthen employee awareness.
- Skyone conducts recurring phishing , providing detailed reports and suggestions for improvement based on risk profile.
4. Use behavioral analysis (UEBA)
- "User and Entity Behavior Analytics" technology detects anomalous (out-of-the-ordinary) behaviors, signaling risks before they materialize.
- Skyone combines machine learning (AI) models with UEBA to identify standard deviations in users, applications, access patterns, and systems.
5. Keep systems updated
- Applying security patches is vital to closing exploitable vulnerabilities.
- With managed services, Skyone ensures continuous updates and monitoring of cloud and on-premises environments , reducing the attack surface.
Use this list to assess your company's level of protection:
- Are all systems patched and updated?
- Is identity control and MFA implemented for all critical access points?
- Is there continuous threat monitoring by experts (SOC)?
- Do employees undergo frequent training and phishing tests?
- Do suppliers and partners undergo safety assessments?
- Is there centralized visibility of cyber risks?
- Does the company have a structured incident response plan?
The cases of Dell, Microsoft, and C&M Software show that prevention is always cheaper than the damage . Furthermore:
- Security is not just technology. It's process, culture, and partnership.
- Having just an antivirus program is no longer enough.
- Companies need to be prepared before a hacker attack happens.
- Protecting the ecosystem of partners and suppliers is just as important as protecting the company itself.
- Investing in managed cybersecurity services is a strategic decision, not just a technical cost.
The recent attacks on Dell, Microsoft, and C&M Software have laid bare an uncomfortable truth: no matter the size of the company, if it's digital, it's a target. And often, the weakest link isn't in the infrastructure, but in the access points, the people, and the connected partners.
Meanwhile, cyberattacks are evolving. Today, cybercriminals use artificial intelligence to automate intrusions , exploit vulnerabilities before they are even documented, and execute increasingly convincing social engineering campaigns.
In this scenario, relying solely on basic measures, such as antivirus software or isolated firewalls, is like locking the front door and leaving the window open.
Skyone has developed cybersecurity for companies that cannot afford to take that risk. Our portfolio goes beyond threat detection: we deliver a complete, ready-to-act cybersecurity defense framework , including:
- Structured Incident Response
- Continuous monitoring with SOC
- Anomaly detection with AI and UEBA
- Realistic phishing simulations and ongoing education
- Protection from the cloud to the endpoints
- Robust identity and access controls
Is your company truly protected against what's to come? Schedule a conversation with our team and discover how to anticipate the next hacker attack before it happens.
Start transforming your company
Test the platform or schedule a conversation with our experts to understand how Skyone can accelerate your digital strategy.




